A new regulatory landscape for digital businesses and providers in the UK
INTRODUCTION
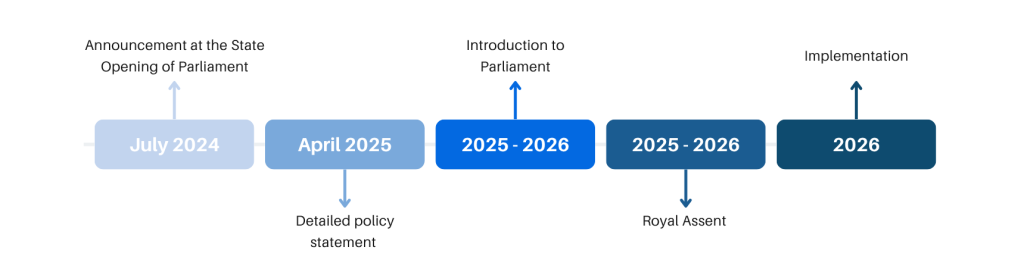
On 17th July 2024, at the State Opening of Parliament, the UK Government announced its intention to introduce the Cyber Security and Resilience Bill, a major legislative effort to modernise the country’s cybersecurity framework. The proposed legislation aims to update the existing Network and Information Security Regulations 2018, known as UK Network and Information Systems (hereafter NIS),[1] reflecting the growing complexity of digital threats and the critical role of technology providers in national infrastructure.
Updates to the NIS regulations are expected to be introduced between 2025 and 2026,[2] marking a turning point for how cybersecurity obligations are defined and enforced across sectors. These changes are designed to improve the cyber security of organisations providing critical services,[3] including energy companies and the NHS, as well as digital services such as cloud computing and online search engines. At Spark Legal and Policy Solutions, we are closely monitoring the development of this legislation to help our clients stay ahead of evolving compliance standards. In this article, we explore the rationale behind the Bill, its key provisions, and the practical implications for companies across the digital economy.
WHAT IS THE CYBER SECURITY AND RESILIENCE BILL 2025?
The Cyber Security and Resilience Bill 2025 (hereafter CS&R) aims to strengthen national cybersecurity by overhauling and expanding the existing NIS Regulations introduced in 2018. The initiative is intended to enhance the UK’s cyber defences and resilience against cyber attacks, seeking to protect infrastructure and critical services used by UK companies by addressing vulnerabilities, and supporting the digital economy in delivering growth.[4]
The upcoming legislative changes are part of the Government’s £2.6 billion National Cyber Strategy, designed to encourage at-risk organisations to strengthen their cyber resilience and contribute to the overall security and development of the UK digital economy.[5]
WHY IS THIS HAPPENING?
The introduction of the Cyber Security and Resilience Bill comes in response to the evolving nature of cyber threats and the limitations of existing regulations. Since the implementation of the NIS Regulations in 2018, major incidents, such as Operation CloudHopper,[6] which affected managed service providers and many organisations simultaneously, have highlighted areas where the UK’s cyber laws may require updates to maintain the protection of vital services and their supply chains.[7]
These events have underscored the need for a more robust and adaptable regulatory framework that can better protect essential services and their interconnected suppliers. The current landscape, shaped by rapid digitalisation and growing reliance on third-party technology providers, demands clearer obligations, faster incident response mechanisms, and stronger government oversight.
SUMMARY OF THE KEY CHANGES
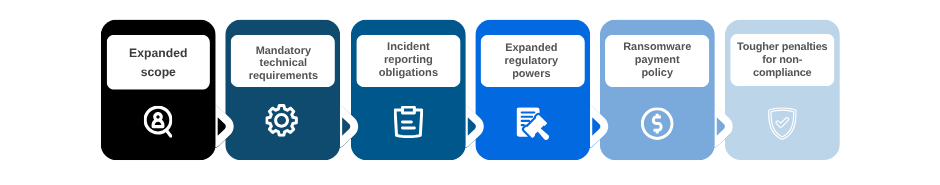
- Expanded scope: More sectors brought under regulation. The Bill brings new sectors and entities into scope: Managed Service Providers (MSPs),[8] Data centres with ≥ 1 MW capacity or operators with over 10 MW combined capacity,[9] Relevant Digital Service Providers (RDSPs),[10] Designated Critical Suppliers (DCS)[11] – suppliers to essential service operators, even small firms. This could include tech startups, B2B SaaS firms, and SMEs previously outside of formal cyber regulation.
- Mandatory technical requirements. The Cyber Assessment Framework (CAF)[12] from the National Cyber Security Centre (NCSC) becomes legally binding for regulated entities. Companies must demonstrate governance, protection, detection, recovery, and continuous improvement.
- Incident reporting obligations. Regulated entities must report incidents related to cyberattacks, data breaches, ransomware, and major disruptions, in two stages[13]: 1) Within 24 hours: initial notification to the NCSC and relevant authority; and 2) Within 72 hours: detailed incident report and, where applicable, customer disclosure.
- Expanded regulatory powers. Government authorities will have the power to set stronger supply chain duties for operators of essential services (OES)[14] and relevant digital service providers (RDSP) in secondary legislation. The Government will also have the capacity to designate specific suppliers as “Critical” (DCS), issue binding sectoral directives, introduce future obligations through secondary legislation, regulators will gain powers to audit, issue penalties, and recover compliance costs.[15]
- Ransomware payment policy. Public sector bodies and critical infrastructure operators will be banned from paying ransoms. Private sector companies must notify the Government before making any ransom payments, ensuring due diligence (e.g., sanctions compliance).[16] The aim is to reduce the incentives for attackers and improve national coordination.
- Tougher penalties for non-compliance. Proposed enforcement actions include fines of up to £17 million or 10% of global annual turnover for serious breaches. Non-compliance could result in operational disruption, reputational damage, and regulatory scrutiny.[17]
WHO WILL THESE CHANGES IMPACT?
The direct impact of this new regulation mainly falls on companies providing critical services. The regulations cover five sectors (transport, energy, drinking water, health and digital infrastructure) and some digital services (including online marketplaces, online search engines, and cloud computing services).
- Public Sector and Essential Services: This category includes national critical infrastructure such as energy, water, transport, and healthcare systems, as well as public sector bodies like the NHS, educational institutions, and local councils. These organisations will face some of the strictest requirements under the Bill.[18] They will be legally prohibited from paying ransoms, must fully comply with CAF, and report any major incident within 24 to 72 hours. They will also be subject to enhanced technical oversight.
- Digital Service Providers and Technology Firms: This group includes MSPs, cloud platforms,[19] SaaS providers,[20] and digital infrastructure firms. These businesses are now explicitly brought under regulatory scope due to their central role in the UK’s digital supply chains. They must comply with CAF, undergo audits, notify incidents to both authorities and customers, and ensure security across their supply chain.
- Data Centres and Infrastructure Operators:[21] Companies operating data centres with at least 1 MW per site or over 10 MW in total will now be directly regulated. They must implement CAF and report disruptions that impact essential services. Some may also be designated as Critical Operators, triggering enhanced regulatory oversight and risk management obligations[22].
- Designated Critical Suppliers (DCS): These are businesses (often SMEs) that supply essential services to regulated organisations (e.g. MSPs, NHS, utilities). Even if not large themselves, they may be designated as DCS by the Government due to the strategic importance of their services, becoming subject to the full set of obligations: CAF compliance, incident reporting, and cyber governance. This also increases client expectations and contract scrutiny.[23]
- General Private Sector (Non-Designated Companies): This group includes startups, SMEs, fintechs, retailers, and other businesses that are not directly regulated by the Bill. They may still be affected indirectly. If they are part of a regulated supply chain, clients may impose cybersecurity requirements contractually. Even outside legal scope, companies are expected to align with frameworks like CAF or ISO 27001.[24] If a private company decides to pay a ransom, it must first notify the Government for clearance (e.g., sanctions compliance).[25]
WHY DOES THIS MATTER?
The CS&R Bill 2025 will significantly affect companies by expanding regulatory obligations to many tech-driven and service-oriented businesses. Startups and SMEs that provide IT services, cloud solutions, data hosting, or software to regulated sectors, such as healthcare, finance, or energy, may now fall under new legal requirements, or face contractual pressure to meet equivalent standards. Even companies not directly regulated may need to comply with incident reporting, adopt the Cyber Assessment Framework, or prove their cybersecurity maturity in order to retain large clients or secure investment.
UK companies will need to anticipate these obligations by strengthening internal cybersecurity governance, revising supply chain contracts, and aligning with recognised frameworks like CAF, ISO 27001, or NIST. Beyond compliance, this also presents a strategic opportunity: early adopters of robust cyber standards will be better positioned for growth, reputation, and partnerships in an increasingly security-conscious market.
TIMELINE AND NEXT STEPS
A detailed policy statement was published in April 2025, outlining the Government’s intentions and scope of the reforms. The final legislation is expected to be formally introduced to Parliament between late 2025 and early 2026.
HOW CAN SPARK HELP?
The CS&R Bill 2025 marks a major shift in how cybersecurity will be governed in the UK. By expanding regulatory scope, introducing mandatory standards, and placing greater responsibility on both essential service providers and their suppliers, the legislation pushes cybersecurity from a technical concern to a legal and strategic priority.
The new regulation will expand compliance expectations across the UK’s digital economy. For UK companies, especially startups and SMEs delivering cloud, SaaS, or IT services to regulated sectors, this means increased scrutiny, new reporting duties, and rising pressure to adopt recognised frameworks like CAF or ISO 27001.
Further details are expected in the coming months, when the regulation is introduced to Parliament. At Spark, we support companies in navigating complex regulatory landscapes, whether through policy reviews, compliance assessments, and tailored legal reports.
Contact us at solutions@sparklegalpolicy.eu for more information, and follow us on LinkedIn to stay informed about the latest developments surrounding the Cyber Security and Resilience Bill!

[1] Network and Information Systems Regulations 2018. Available at: The Network and Information Systems Regulations 2018
[2] More information available at: Cyber laws updated to boost UK’s resilience against online attacks – GOV.UK
[3] Critical services are essential goods, systems, or services that form part of the UK’s vital national infrastructure or digital ecosystem. These services are considered strategically important because a disruption, cyber breach, or operational failure could significantly impact national security, public safety, economic stability, or the continuity of essential public functions.
[4] More information available at: The NIS Regulations 2018 – GOV.UK
[5] Cyber laws updated to boost UK’s resilience against online attacks – GOV.UK
[6] Operation CloudHopper was a large-scale cyber espionage campaign uncovered around 2017, attributed to a Chinese state-sponsored hacking group known as APT10. The operation specifically targeted Managed Service Providers (MSPs), companies that offer IT, cloud, and infrastructure support to other organisations.
[7] https://www.skadden.com/insights/publications/2025/06/uk-bill-would-increase-cybersecurity?utm_source=chatgpt.com
[8] Managed Service Providers (MSPs): Companies that manage IT services for other businesses. For example, a company that handles cybersecurity for a hospital or bank. They support critical services.
[9] Data centres with a capacity of 1 MW or more. An operator that manages multiple data centres will fall under regulation if the combined total capacity across all sites exceeds 10 MW.
[10] Relevant Digital Service Providers (RDSPs ): Companies that offer essential digital services to businesses and the public. Under the original NIS Regulations, this typically included: online marketplaces, online search engines, cloud computing services.
[11] Designated Critical Suppliers (DCS): Third-party suppliers to the CSPs, that provide products or services considered essential to the functioning of critical infrastructure or regulated entities.
[12] The Cyber Assessment Framework (CAF) is a structured set of principles developed by the UK’s National Cyber Security Centre (NCSC) to help organisations assess and improve their cyber resilience. Available at: Cyber Assessment Framework – NCSC.GOV.UK
[13] Cyber Security and Resilience Policy Statement
[14] Operators of essential services (OES): are organisations that provide services which are essential for the maintenance of critical societal or economic activities. These include energy, transport, drinking water, healthcare, and certain digital infrastructure services.
[15] UK Bill Would Increase Cybersecurity Standards for Critical Infrastructure Operators | Insights | Skadden, Arps, Slate, Meagher & Flom LLP
[16] UK government to ban public bodies from paying ransoms to hackers | Cybercrime | The Guardian
[17] Get Compliant – New 2025 Cyber Security And Resilience Bill
[18] UK government to ban public bodies from paying ransoms to hackers | Cybercrime | The Guardian
[19] Companies that provide the infrastructure and tools for running applications and storing data online.
For example, a business might use a cloud platform to host its website or store customer data securely.
[20] Companies that offer software applications over the internet, usually by subscription. For example, a company might use a SaaS tool for managing customer relationships, sending emails, or handling payroll.
[21] For example, commercial data centre company hosting NHS medical records; a colocation facility serving government cloud services.
[22] Cyber Security and Resilience Policy Statement
[23] Cyber Security and Resilience Policy Statement
[24] Developed by the International Organization for Standardization (ISO), it provides a globally recognised standard for Information Security Management Systems (ISMS).
[25] UK Confirms Ban of Ransomware Payments to Public and Critical National Infrastructure Sectors
